If you’re like me, you have a lot of different systems running in different places: at work, at home, in the lab, and in the cloud. And if you’re like me you’ve often struggled to connect and access these machines, especially when you’re on the road. At long last, I have a fully functional solution that lets me access everything from everywhere, securely and efficiently, whether on the open internet or behind NAT after NAT. The solution is ZeroTier!
Connectivity Challenges of the Modern Nerd
I have a variety of computer systems I like to access, and most are inherently inaccessible. Some of this is incidental, thanks to NAT and consumer telcos, but I’m also careful to lock them up with firewalls and access controls. I’ve been searching for a reliable, friendly, and secure way to access everything from everywhere since forever, and I finally have just the thing up and running!
Here’s a rough inventory of the systems I’m trying to access, and why it’s hard to get to them:
- My home network is served by two unreliable consumer ISPs (Spectrum and Windstream), each with its own NAT. These are fed to a pfSense router with another layer of NAT, but I often switch ISPs as one falls on its face. Inside my home I have a firewalled VLAN for IoT devices and another for my home lab. I’ve also got a big TrueNAS file server, some Macs, a few Ubuntu machines, and a Home Assistant instance.
- My office has amazing high-speed connectivity but the building router is inaccessible to me and feeds my office pfSense with two layers of NAT. Here again, I’ve got a firewalled VLAN for my office lab machines, along with a bunch of Macs, a file server, a few more Ubuntu machines, and another Home Assistant instance.
- My web servers run in Linode using Docker and are well firewalled.
- My mobile clients include my new 14″ M1 MacBook Pro, my trusty iPad Pro, and my iPhone. I’m often connected using mobile data of course, but I also sometimes use Wi-Fi at hotels, family, or work spaces.
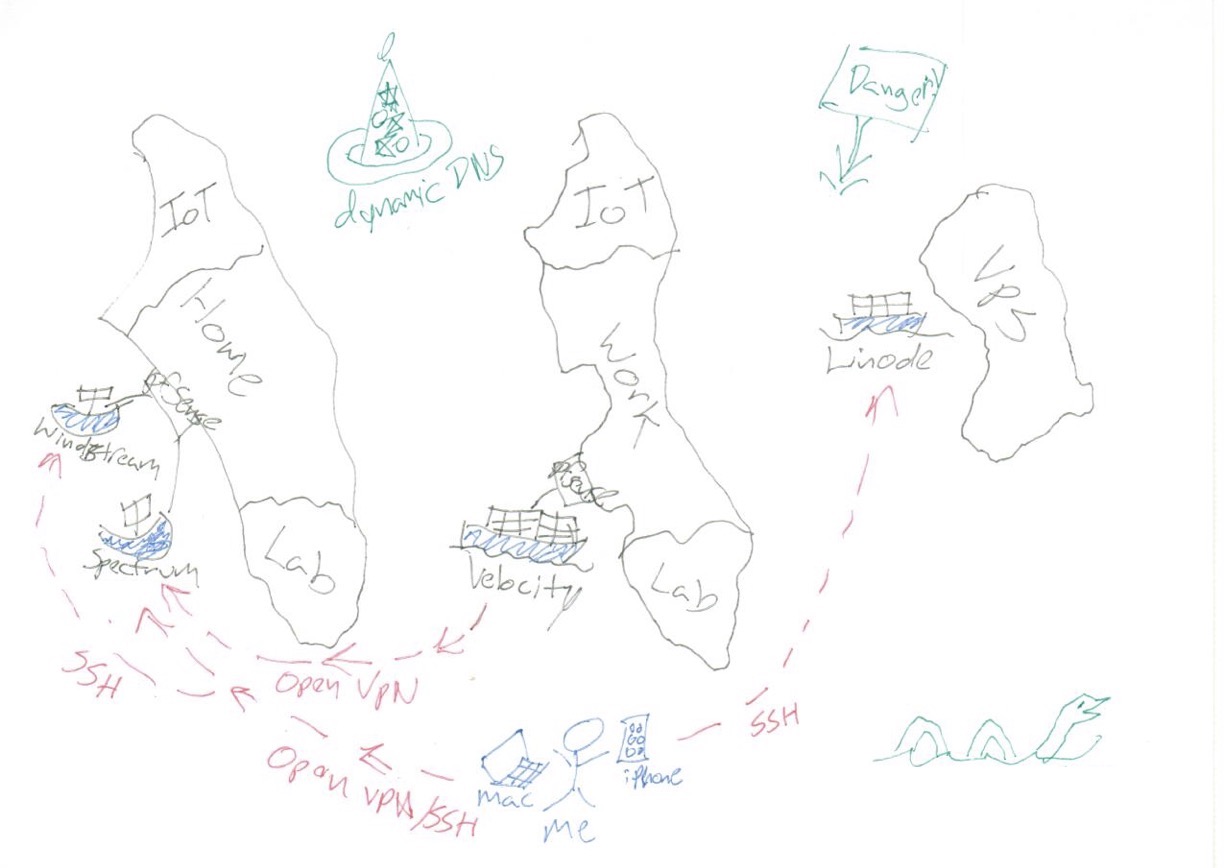
The challenge, put simply, is how to be able to connect to my home network, my office, and my web servers from any of my mobile clients, regardless of the connectivity available at each location. And how to keep it all secure so my remote access doesn’t let others get in and mess up my stuff!
By far the biggest issue is all that NAT. If you’re not familiar with the issue, network address translation (NAT) “hides” a private network behind a single IP address, dynamically routing connections to the right client. This is why so many home and office routers use IP addresses beginning with 192.168 or 10: They’re NATting this private network. The problem is that some services (especially if they deal with incoming connections) need a public IP address or at least a public port. But some routers don’t “do” UPNP port assignment right, and even if they do you still need a dynamic DNS provider to deal with dynamic IP addresses. Remote access behind NAT is a mess, and it’s even worse when you have NAT behind NAT and no access to any of the routers!
NAT, DNS, and firewalls also pose a serious challenge on the client side. It’s sometimes hard to get back to an open port since some providers block access to well-known VPN ports or IP addresses or force the use of their own DNS resolver or other client “services” that muck up the works.
There are many remote access services and VPN providers, but these don’t solve the issues completely. It’s hard to set up a VPN server behind a NAT in the best circumstances and nearly impossible behind double NAT, especially if you don’t control the router. And remote desktop solutions tend to have limited client support, over-reliance on UPNP, or are system resource hogs.
Up to now, the only moderately-reliable connectivity scheme I’ve had was a combination of OpenVPN and SSH. Because I was able to control my home routers, I could set up an OpenVPN service on my home pfSense, punching through both NATs with a private port and using a dynamic DNS provider to locate the IP. Then I set up an OpenVPN client at work, which connected outbound through double NAT to my home network. I provided access to my client devices using another OpenVPN server and OpenVPN clients for iOS and macOS. I provided backup access using an SSH endpoint at home on a high port. This solution worked, but was incredibly finicky. And since the world can see my dynamic DNS hostname, I had to be very careful to secure it.
ZeroTier Changes Everything
Once I started playing with ZeroTier, I realized that it could do everything I wanted and more.
The most powerful aspect of ZeroTier is that it is designed to punch through NAT, firewalls, and dynamic network infrastructure from the inside out. There are no static accessible servers – everything is a client and everything connects to the ZeroTier service before turning around and accessing your other resources over a private network.
And rather than playing around with high-level services, ZeroTier connects everything with a simple virtual layer-1 and 2 Ethernet network. It provides some higher-level services (IP addresses and DNS) but it doesn’t even pretend to be a remote access service. It’s a virtual network connection, and you can run anything on top of it.
It’s also incredibly robust and secure, with end-to-end 256-bit encryption and a “zero trust” design so your network is your own. And it runs on pretty much everything, from Linux to macOS and iOS to Windows and Android. It’s even available as a plugin for Home Assistant, Mikrotik/OpenWRT, and many NAS operating systems! It’s not yet robustly supported by TrueNAS or pfSense, but I expect that will come with time.
I was able to get ZeroTier up and running in just a few minutes, and it provided robust and reliable access to everything while I was out of the country on dodgy internet for a month. I was even able to set up a private “home run” back to the USA so my Apple TV worked! In fact, ZeroTier was the most reliable part of my infrastructure over this time, punching through a triple-NAT-quadruple-Wi-Fi-Repeater sandwich and quickly coming back online through reboots and outages from various other components.
ZeroTier is not perfect, however. It is unapologetically nerdy, with heavy reliance on CLI commands and an assumption of network and system administration competence. And the new DNS feature really needs work. But even with minimal documentation I was able to get everything up and running, and I expect my readers could do the same!
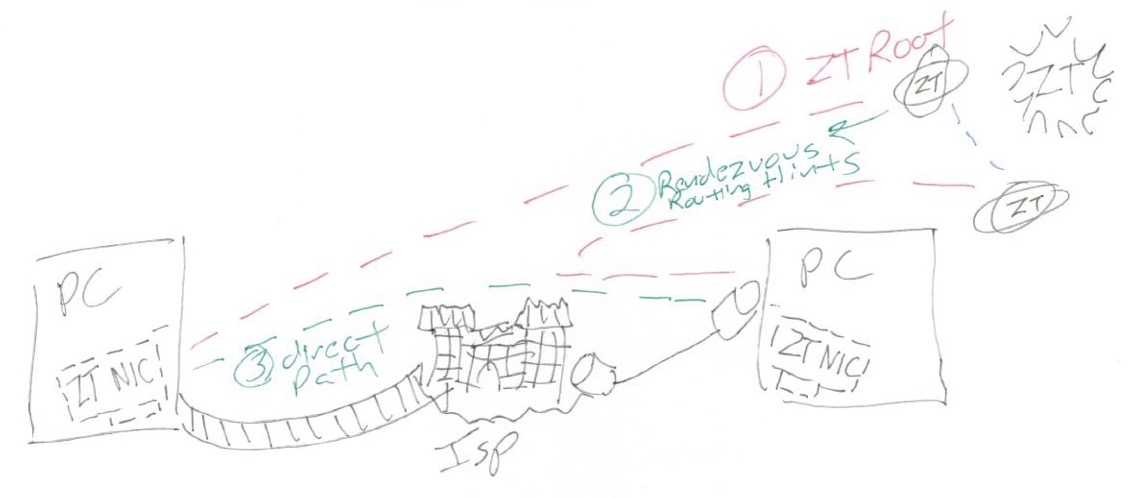
One of the criticisms of ZeroTier is that, although it is fundamentally a peer-to-peer network, it relies on root servers operated by the company to enable connectivity. But this is really a philosophical rather than a technical issue, since nearly every service relies on some root nodes, from DNS to the internet itself, and ZeroTier actively tries to “get out of the way” by encouraging direct peer-to-peer connectivity for performance reasons. Additionally, the system is designed with “zero trust” end-to-end encryption, so your data is isolated from any other users of the network.
Operationally, setting up a ZeroTier network is incredibly simple:
- Create a ZeroTier account on ZeroTier Central
- Provision your own network using their web interface, including setting IP address ranges
- Install the ZeroTier One client on any device and enter your network ID
- Accept the client into your network using the web interface and configure an IP address for it
Once a client is added to your network, you can access it from any other network client as if they were on the same LAN. It’s really that easy, and in my experience works through anything and from anywhere!
More advanced users can set up DNS or routing within their ZeroTier network, allowing it to act as a full-blown VPN. But even without these features enabled, the VPN-like iOS and macOS client enabled me to use my servers and access my systems using IP addresses.
Note: ZeroTier is presenting at Networking Field Day in January, 2022! Tune in Thursday, January 27, at 1 PM Pacific time for a technical deep dive into ZeroTier with some of the smartest people in enterprise networking. We’ll also post recordings of the session on the Tech Field Day YouTube channel shortly after. Although this is my company and event, I “discovered” ZeroTier independently and this article was not sponsored or influenced by this sponsored event in any way!
Stephen’s Stance
It is rare that I am so enthusiastic about any service, but ZeroTier does exactly what I needed. With very little effort, I was able to access the key components of my infrastructure from any device, regardless of network configuration or availability of IP addresses or ports. And everything I’ve tried to do (from the Home Assistant UI to SSH to SMB file transfer) has worked flawlessly and efficiently. Apart from the fidgety user interface, ZeroTier is the answer to my connectivity prayers!
I’ve been using Zerotier for the last 4 years, it works great.
In case or very unreliable connections, like satellite links to cruise ships, try https://mosh.org/ instead of ssh to provide a better experience.