Never enter login or password information anywhere but the intended location!
After a decade of this warning, why would people enter their username and password or financial account information on random web sites? Maybe it’s because the very entities who are supposed to be concerned about identity theft and fraud just keep trying to train consumers to do exactly what they’re not supposed to do?
Do’s and Don’ts
This has got to stop. Technical workarounds (secure tokens, credit monitoring, freezes, fraud limitations, insurance, etc) will only get us so far against social engineering. No amount of security will protect a customer who willingly gives up his account information to a scammer. The only way to fix the situation is to tighten valid processes enough so consumers know not to trust anything else.
Here are a few suggestions for consumer-facing businesses:
| Don’t | Do | Why? |
|---|---|---|
| Ask customers to click on links in email messages to get to login pages | Ask customers to type in your valid URL and log in from there | You are training them to respond to spam phishing attacks |
| Call customers and ask for their account number, password, PIN, and other information | Ask customers to call you using the number printed on their credit or identification card | You are training them to accept unsolicited and unverified contacts |
| Leave voicemail or email messages telling customers to contact you on an unknown phone number or web site | ||
| Repeatedly ask customers for the same information as you transfer them from one phone line to another | Only ask for the information needed when it’s needed | It devalues the credentials and teaches them to hand them out to anyone who asks |
| Use alternative domains names for account access | Keep everything under one familiar banner | You are telling them it’s OK to give their account credentials to third parties |
| Ask for information that you obviously aren’t verifying or using | Only ask for what you need, and make sure it’s valid | You are telling them you don’t really care about security |
I’m not a security expert. I’m just a guy who doesn’t like seeing people trained to do dumb things like giving up their account information to random people who phone or email them.
Some Examples
Why am I posting this today? Because just today I have been exposed to two such insecurities, and I’ve had it. Here are some examples of laughably insecure processes I’ve seen lately. The names have not been changed because these folks are not innocent. They should fix these problems, not pretend this is accepted practice.
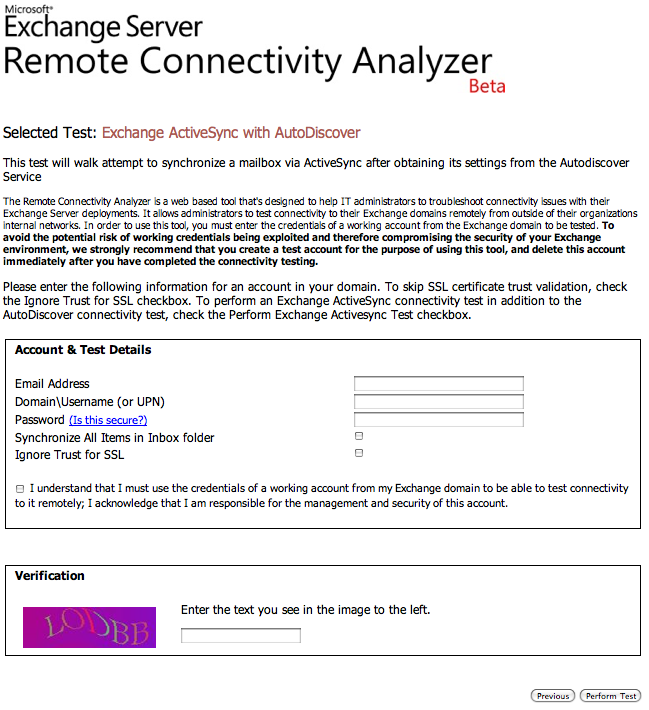
- A reader suggested verifying Microsoft Exchange access by using a site called testexchangeconnectivity.com. I had never seen this site, so I assumed it was spam. Before deleting the suggestion, though, I looked at it (using a secure server) and was shocked at what I found there. This seems to be a legitimate Microsoft site on a totally off-the-wall domain name without the normal corporate wrapping, yet it asks for your Exchange credentials! The instructions say to use a test account and delete it after, but everyone knows what joe-user is going to do. You should never enter valid Exchange credentials into a random web site. Why not move this service to a microsoft.com domain and wrap it with the familiar (if annoying) corporate look and feel?
-
VoIP folks were excited to see SIP provider Gizmo5 offering free unlimited calling and integration with Google Voice. The catch? You had to hand over your valid Google account login name and password. Then Gizmo5 started changing the rules, limiting calling time and charging for the free connectivity. Your google account should be protected like your debit card PIN since it is key to so many services these days!
-
Twitter’s email notifications for new followers stink, so Twimailer stepped in with a better replacement. But you had to replace your real email address in your Twitter profile with a twimailer.com address. Bad idea! That same email is used to verify your account and recover your password! Always retain control of email addresses used for verification!
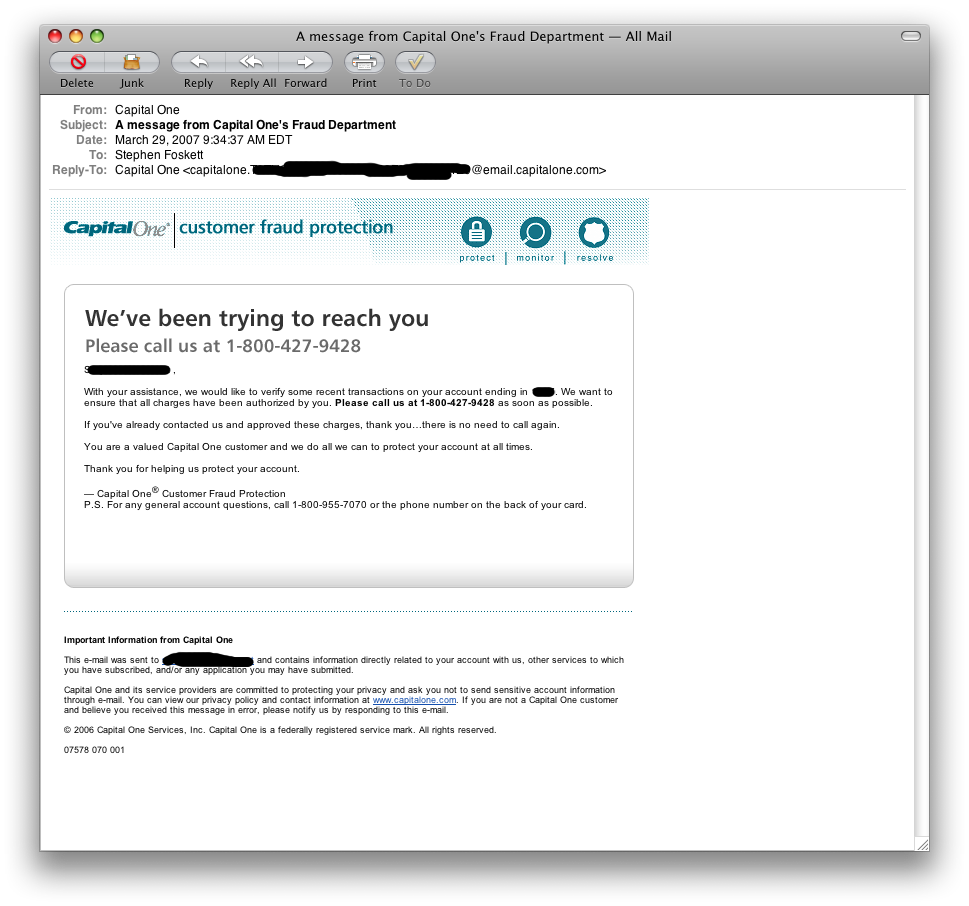
- I complained like crazy about this one! Capital One’s fraud department uses an unlisted 800 number and uses email and voicemail asking you to call. Of course they then ask for all sorts of personal financial and travel details. Never call an unknown number and give out personal information! How about including the fraud department phone number on the back of the card or on the monthly statement and telling people to call the number listed there? I always just call the main number and ask the operator to transfer me.
-
It is impossible to call AT&T and not have to give up personal information multiple times. Enter it in the phone and you’ll just be asked for it again. What is the point? Then they’ll forward you to another department and guess what they ask for? Yes, they want your personal information again!
-
I needed a cashier’s check as part of a mortgage refinance (yay, low interest rates!) so I went to my local National City bank branch. I filled out the form the teller had, she looked up my account based on my name, and I walked out with something as good as cash. One problem: She never asked to see my ID or otherwise verify who I was! It turned out that I didn’t need the check after all, so I returned to the bank, handed over the check, and a different teller deposited it in the account I provided. Yes, that’s right folks, no one ever checked my ID as I transferred thousands of dollars into and out of accounts based solely on the name I gave them!
- The Hilton Hotels web site annoys me in three ways. And this isn’t just some hotel web site: Once one is logged in they get access to an account that allows the use of credit cards and hotel points that function as money!
- For some reason, login doesn’t always work: I enter my correct, valid username and password and I am redirected to another login form. I enter the correct, valid information here and I am redirected to yet another different login page. If I enter my information here, I can log in. That second page never works, but I have to enter something or I can’t get to the third, functional page. Why have three different login pages? Why doesn’t it always work?
- Hilton has dozens of domain names, and a standard session (log in, find a hotel, book a room) includes at least four different domains. I get branding, but I also know that Hampton, Embassy, and Hilton are one company. Why confuse the issue with multiple domain names?
- Hilton uses two different but equally valid usernames and passwords! One can log in with either a self-selected username or an assigned “hhonors number” and either a password or a PIN! A casual observer ought to see how this weakens security.
What are these supposedly-respectable businesses thinking? They are training consumers to accept poor security! They are undermining the system, making us all less secure. And we wonder why fraud and identity theft has become so common that valid credit card numbers are literally a dime a dozen on the black market!
It would be nice to see it coming from a microsoft.com domain but the site isn’t meant for Joe User. It is invaluable for engineers troubleshooting exchange CAS, people who know how to perform an RDNS lookup, verify the cert, check whois etc. The site is also reference from http://support.microsoft.com/kb/982907.